Ever wonder how the massive organizations we rely on protect their entire digital kingdom from the bad guys? It all comes down to one crucial device: the firewall. It’s the unsung hero, the digital bouncer, and the grumpy gatekeeper all rolled into one.
Think of it this way: to get into your home, a visitor needs a key or a door code. To drive your modern car, you might need a digital key that restricts how the car can be driven. A firewall is the digital version of this crucial security layer, only it protects your network and data from all the chaos floating around the internet.
The Digital Gatekeeper: How a Firewall Works
The name “firewall” itself is a great metaphor. In the physical world, a firewall is a barrier built to stop a fire from spreading. In our digital world, it does the exact same thing—it stops unauthorized access from spreading into your network and computer systems.
At its core, a firewall implements a simple but effective set of rules. Some data packets are allowed (green) and others are denied (red). The below image depicts this
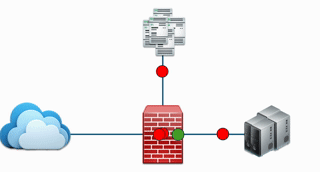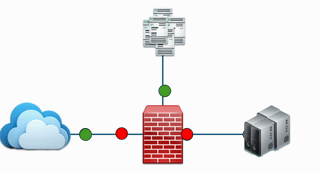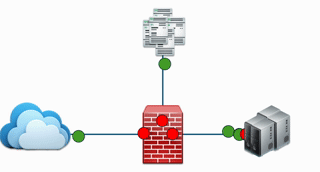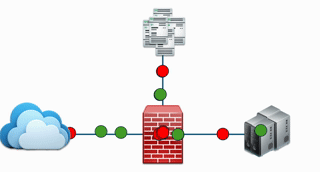
The firewall makes this decision by looking at three main things:
- Source: Where the traffic is coming from.
- Destination: Where the traffic is trying to go.
- Port: The specific “door” the traffic is trying to use. For example port 80 for basic web traffic or port 443 for secure web traffic
These rules should always follow the Principle of Least Privilege. This means you only allow the required traffic needed for an application to function or for the user to do their work, and nothing more. It’s like only giving your houseguest the key to the front door, not the keys to your car, your neighbor’s garage, and your safe deposit box. It’s not about being mean; it’s about being smart and secure.
The Evolution: From Bouncer to Digital Detective
A basic firewall is fantastic for keeping out the common riff-raff, but the modern internet demands more. What if you need to look deeper into the data packet? What if you want to know what specific website a user is accessing, or even who the logged-in user is?
That’s where the Next-Generation Firewall (NGFW) comes in.
An NGFW is less of a bouncer and more of a digital detective. While a traditional firewall only looks at Layer 3 and 4 attributes (IP address and port number—like checking a name and a zip code), an NGFW digs deep into Layer 7 application attributes.
The NGFW Advantage
A traditional firewall might see traffic on port 443 (encrypted web traffic) and just say, “Looks good, pass!” An NGFW can look inside that traffic and say:
- “That’s Susan from accounting.”
- “She’s using the Dropbox application.”
- “She’s trying to upload sensitive company data to a personal account.”
- “DENY.”
This deep-level inspection allows organizations to make decisions based on the user identity and the application itself, not just the location. This power makes the NGFW your strongest first line of defense against the digital wild west.
In a nutshell, whether you’re using a basic firewall for your home or an advanced NGFW for a massive company, it is your digital gatekeeper. Make sure yours is turned on and correctly configured. It is the single most crucial step in protecting your digital castle!